5 Surprising Truths About Cyberattacks on Hotels
Introduction: The Hidden Risk Behind Every Reservation
Every time we book a hotel, we hand over our name, travel dates, phone number, email, and credit card without a second thought. We expect it to be handled safely, quietly, professionally.
But behind that simple confirmation message, there is something else happening.
There is a silent digital battle for your data, and the hospitality industry is one of the easiest battlegrounds.
Most people imagine cyberattacks as brute-force attacks smashing into firewalls. The reality is far more unsettling. Today’s attackers do not break in. They log in.
- They use stolen credentials.
- They exploit trusted systems.
- They impersonate hotel staff.
- And they turn customer service itself into a weapon.
This is not about one website getting hacked. It is about an entire industry being quietly infiltrated.
Here are the five truths no guest sees and many hotels underestimate.
Truth #1: Hackers Aren’t Breaking In. They Are Logging In.
Attackers are not cracking passwords in dark basements with futuristic tools.
They are shopping.
Stolen usernames and passwords are sold in bulk on cybercrime forums for just a few dollars each. These credentials often come from breaches that happened months earlier on unrelated websites or infected personal devices.
By the time a hotel is affected, the breach already happened somewhere else.
Once criminals have a valid login, they simply sign in to hotel systems or partner portals such as Booking.com — exactly like a real staff member.
From that point on, everything looks normal.
Security systems do not usually raise alarms when they see:
- Correct username
- Correct password
- Normal login behaviour
This is what makes credential-based attacks so dangerous.
The system does not think it is under attack.
It thinks it is helping a colleague.
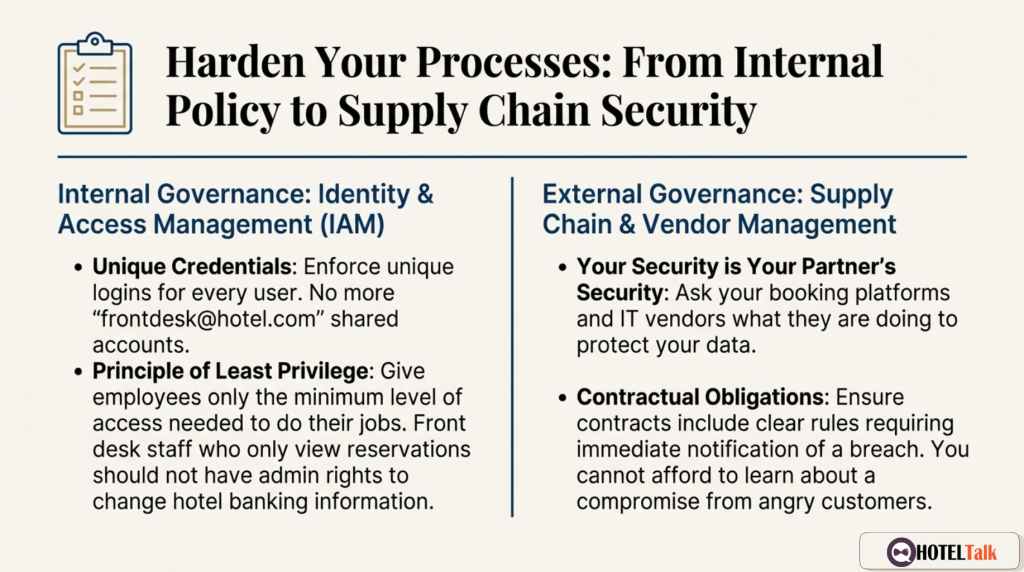
Truth #2: Your Trusted Partners Are Your Weakest Link
Hotels do not operate alone.
They rely on a complex ecosystem of:
- Booking platforms
- Payment processors
- Cloud services
- Channel managers
- Third-party vendors
That convenience creates risk.
The moment attackers compromise one partner system, the impact can spread rapidly.
The now-infamous “I Paid Twice” scam works because criminals access partner portals and then contact guests with real booking information:
- Guest name
- Stay dates
- Reservation code
At that stage, the message is almost impossible to doubt.
It feels real.
Because it is… mostly real.
Only the payment link is fake.
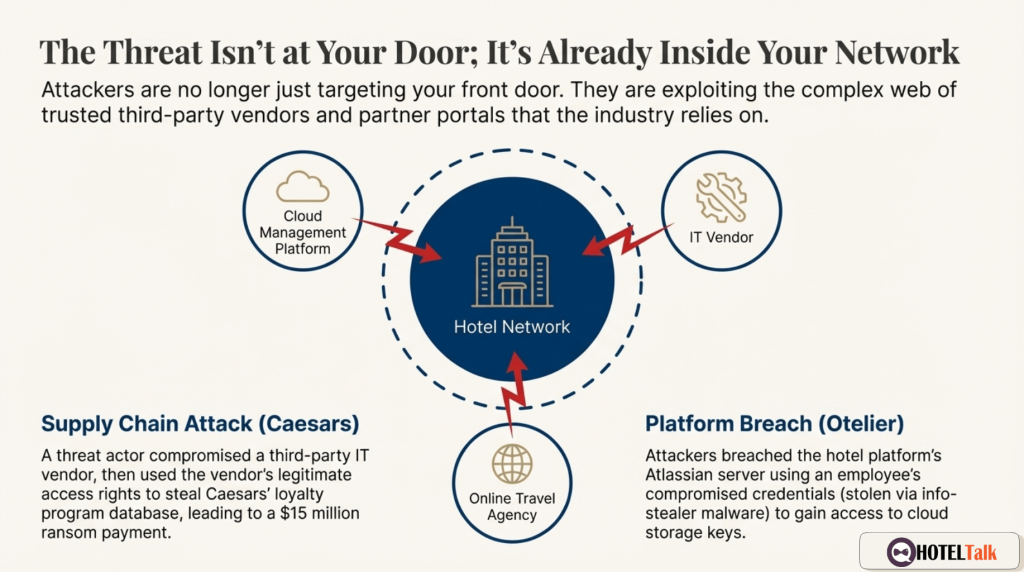
The same pattern appeared in the Caesars breach:
Attackers did not break into the casino directly.
They infiltrated a third-party IT provider first — then moved sideways into Caesars’ systems.
This is supply-chain compromise in action.
Hotels might lock their own doors perfectly…
While their vendors leave the window open.
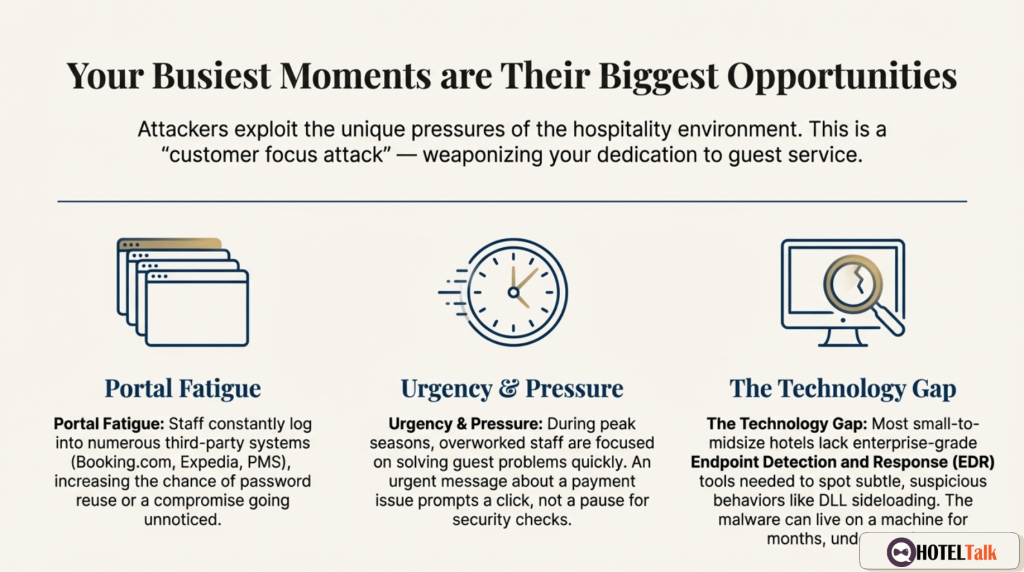
Truth #3: Hospitality’s Culture Is Being Weaponised
Hotels are trained to:
- Help quickly
- Solve problems
- Act fast
Attackers exploit that instinct.
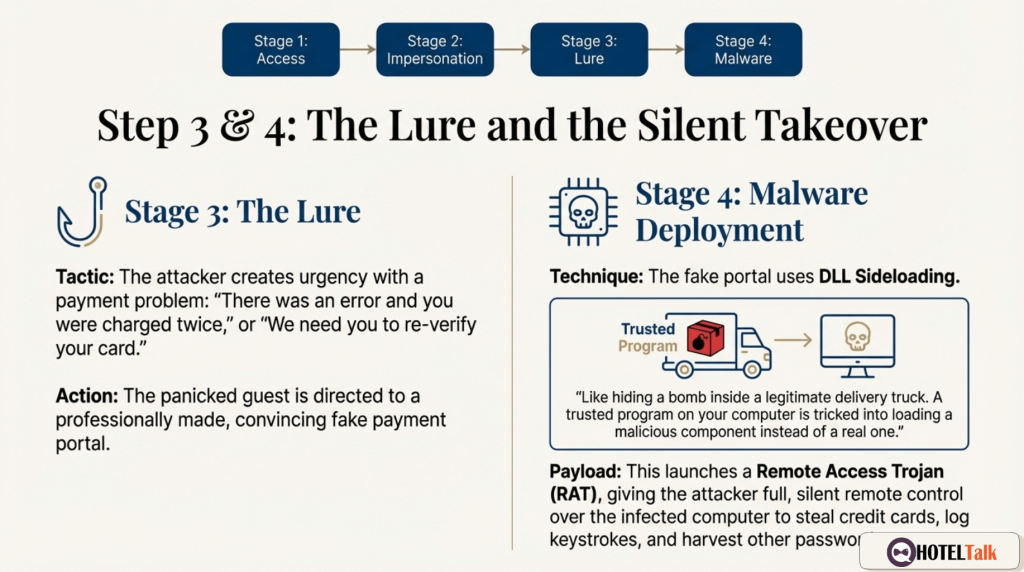
Fake messages are written to create urgency:
“I was charged twice”
“Payment failed”
“Last-minute family booking”
“Urgent reservation issue”
“Special request attached”
These messages push staff into reacting instead of verifying.
During high-pressure periods — holidays, conferences, busy check-in windows — risk multiplies:
- Phones ringing
- Emails flooding in
- Guests waiting
- Staff rushed
That is when mistakes happen.
That is when attackers strike.
In both the MGM and Caesars cases, criminals also used phone impersonation — convincing internal teams to reset passwords or grant access.
Not through hacking.
Through acting.
The art of hospitality became the weapon.
Truth #4: This Is Not Just a Scam. It Hijacks Computers.
The fake payment page is only the opening act.
The real goal is control.
The page can deliver malware using a technique called DLL sideloading:
- A trusted program launches
- A malicious file hides inside it
- The system trusts it — and runs the malware
It is like hiding a bomb inside a delivery truck.
Everything looks legitimate.
The gate opens.
The damage happens inside the building.
Once infected, spyware installs a Remote Access Trojan (RAT).
This gives attackers:
- File access
- Password theft
- Keystroke logging
- Webcam surveillance
- Banking access
- Corporate system control
One fake booking link can become a full digital takeover.
And the victim never knows.
Truth #5: Weak Security Is Now a Legal Risk
Hotels are no longer punished only by guests.
They are punished by regulators.
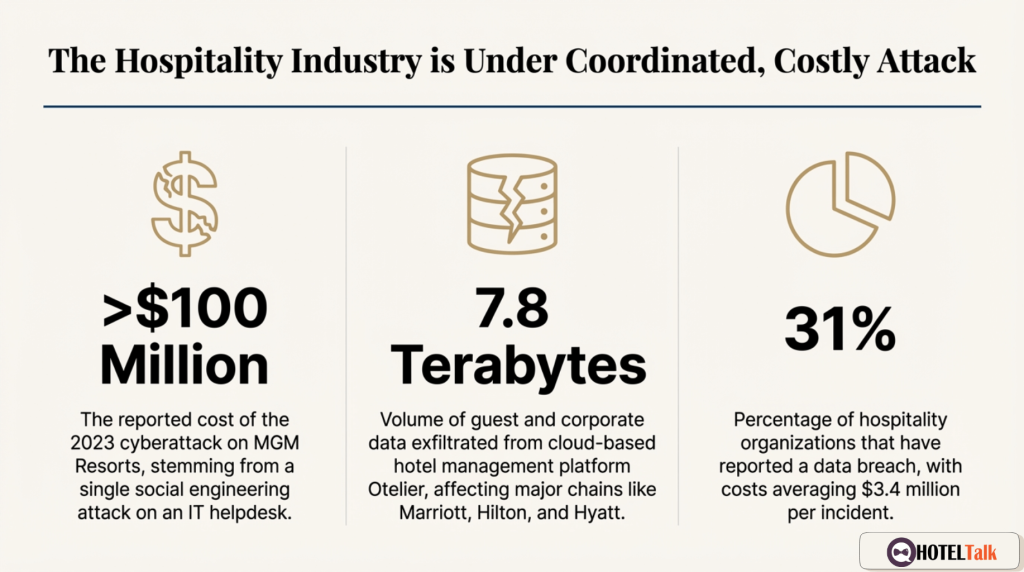
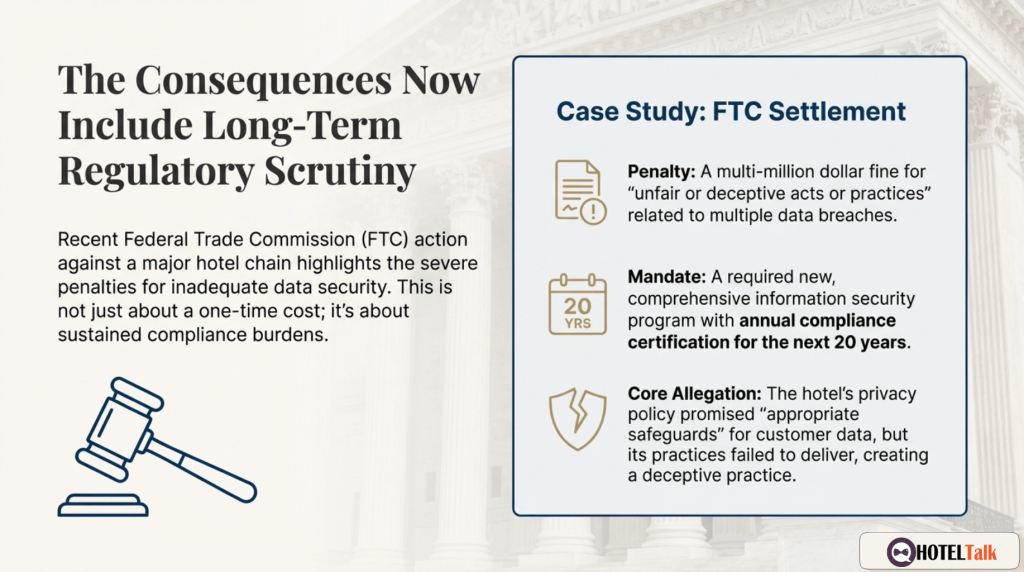
The U.S. Federal Trade Commission has already forced a major hotel group into a multi-million-dollar settlement for failing to protect guest data.
The ruling was based on one phrase:
“Deceptive practice.”
The company promised protection.
Then failed to deliver it.
The government cited failures including:
- No multi-factor authentication
- Outdated systems
- Weak access controls
- No breach monitoring
- Poor account management
- No internal containment strategy
The result?
Massive fines.
Two decades of enforced oversight.
Cybersecurity is no longer “IT”.
It is:
- Legal
- Contractual
- Reputational
- Permanent
The Breach That Fueled the Ecosystem
One breach flooded the criminal economy with fuel.
The compromise at Otelier exposed millions of credentials used across hotel systems worldwide.
These stolen identities now power:
- Partner portal hijacks
- Fake payment scams
- Account takeovers
- Malware chains
One breach does not stop at one company.
It multiplies.
Final Thought: Defense Is Not Enough
The hospitality industry is no longer under attack at the firewall.
It is under attack at:
- The login screen
- The helpdesk phone line
- The booking platform
- The staff inbox
- The partner network
- The guest’s laptop








Security is now a business function, not an IT setting. For hotels, resilience replaces reaction vs For guests, verification replaces trust. Because in today’s world: Attackers do not announce themselves. "They arrive wearing a uniform."
